关键词:
网络工程师成长日记373-李宁公司项目
这是我的第373篇原创文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人

网络设备割接工程项目技术回忆录
网络环境拓扑图如下:
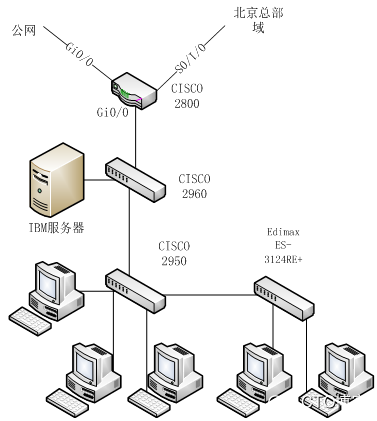
图1 上面的2台为IBM的服务器,白色为协转,再下来是28,再下面是交换机

图2 接×××线的设备就是这次担当替代品的2621

李宁西安分部现行的网络环境是:一台CISCO28系列路由器,2T的S口通过协转接电信的光纤通往北京总部,其上承载着李宁公司整个域的一个管理
西安分部的人必须通过到北京域的验证才能成功登陆到李宁的域,Gi0/0口接光纤直接连到外网, Gi0/1接口下配置n多子接口做单臂路由分别对应不同的部门
Gi0/1口下接一台CISCO2960的F0/24口,2960的F0/24口配TRUNK,native vlan 10,其他接口下access mode都做DOT1X认证,配置有vlan 10 的svi地址,默认网关指的是28路由器
还配有radius-server,F0/23接口TRUNK下接另一台CISCO2950,2950也配有vlan 10的svi地址,默认网关指向路由器,配有radius-server,其他接口下做DOT1X认证,有个接口接了台爱迪麦斯 Edimax ES-3124RE+的24×××换机用来拓展接口。
这里只有IBM服务器和财务部是直接连接公网并不通过域的。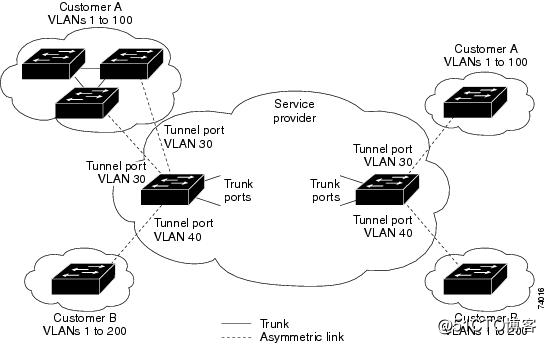
组图3 EDIMAX,这次去长见识了,以前我从未听过有此品牌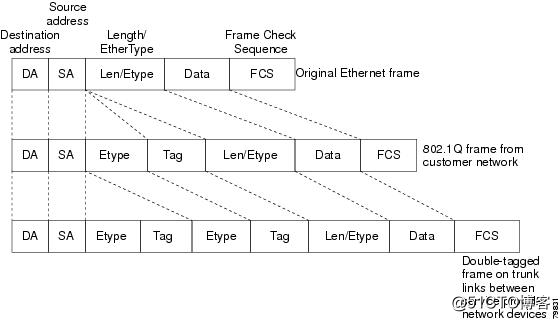
我要做的工作就是:
1把现在的28路由器的配置抓取下来,以供比对刷进用来替代的2621里,并把2950、2960的配置抓下来,以供研究为什么换上26之后网络不通
2把28的线拔下来接到2621上,测试非域内网络状况,结果畅通
3测试域内网络状况,结果不通,排查原因,让域成员离开域再进域重新认证,最终畅通
4把2621上架,回收28路由器
5再次反复测试整个网络的畅通情况,一切正常
6清理现场为我们进来之前的状态
就这么几步,要说基本没什么难度,和传说中的大相径庭。
做完之后,我觉得如果真是这么简单的话,怎么可能第5次去才搞定,所以仔细询问王老师每一次的经过,出现的问题,以及是怎么结束的,记忆中是这样:第一次是因为2T模块插上认不到,第二次是IOS问题,第三次是换上26非域内网络畅通,第四次是换上26域内域外网络都不通,并且vlan间路由ping不通。Vlan间路由ping不通,这个就是真正问题的疑点,我继续询问王老师,王老师说和北京那边的网管沟通后,北京的网管说配置是没有任何问题的,可能是36的单臂路由支持的不是很好,我对网管的这个解释unbelievable.
在坐车回来的路上,我一直在想着网管的解释,想着36的单臂路由之间为什么路由会不通,怎么想都觉得不可能,想着想着,突然想到,单臂路由中不是还配了native vlan吗?配了native vlan的话不就得敲vlan dot1q tag native吗?不敲就有可能不通的,尤其是在我敲试验的机架上,不敲是绝对不通的,用的刚好也是36,于是推断,问题的最大可能性,就是没有敲这条命令导致native vlan的信息传丢了网络不通。
关于native vlan的这条命令到底是什么,CISCO的官网给出的解释是以下链接http://www.cisco.com/en/US/docs/switches/lan/catalyst6500/ios/12.2SXF/native/configuration/guide/dot1qtnl.html
对于脱机的朋友,我把原文粘贴如下:
1.Understanding How 802.1Q Tunneling Works
802.1Q tunneling enables service providers to use a single VLAN to support customers who have multiple VLANs, while preserving customer VLAN IDs and keeping traffic in different customer VLANs segregated.
A port configured to support 802.1Q tunneling is called a tunnel port. When you configure tunneling, you assign a tunnel port to a VLAN that you dedicate to tunneling, which then becomes a tunnel VLAN. To keep customer traffic segregated, each customer requires a separate tunnel VLAN, but that one tunnel VLAN supports all of the customer‘s VLANs.
802.1Q tunneling is not restricted to point-to-point tunnel configurations. Any tunnel port in a tunnel VLAN is a tunnel entry and exit point. An 802.1Q tunnel can have as many tunnel ports as are needed to connect customer switches.
The customer switches are trunk connected, but with 802.1Q tunneling, the service provider switches only use one service provider VLAN to carry all the customer VLANs, instead of directly carrying all the customer VLANs.
With 802.1Q tunneling, tagged customer traffic comes from an 802.1Q trunk port on a customer device and enters the service-provider edge switch through a tunnel port. The link between the 802.1Q trunk port on a customer device and the tunnel port is called an asymmetrical link because one end is configured as an 802.1Q trunk port and the other end is configured as a tunnel port. You assign the tunnel port to an access VLAN ID unique to each customer. See Figure?17-1 and Figure?17-2.
Figure?17-1 IEEE 802.1Q Tunnel Ports in a Service-Provider Network
Figure?17-2 Untagged, 802.1Q-Tagged, and Double-Tagged Ethernet Frames
When a tunnel port receives tagged customer traffic from an 802.1Q trunk port, it does not strip the received 802.1Q tag from the frame header; instead, the tunnel port leaves the 802.1Q tag intact, adds a 2-byte Ethertype field (0x8100) followed by a 2-byte field containing the priority (CoS) and the VLAN. The received customer traffic is then put into the VLAN to which the tunnel port is assigned. This Ethertype 0x8100 traffic, with the received 802.1Q tag intact, is called tunnel traffic.
A VLAN carrying tunnel traffic is an 802.1Q tunnel. The tunnel ports in the VLAN are the tunnel‘s ingress and egress points.
The tunnel ports do not have to be on the same network device. The tunnel can cross other network links and other network devices before reaching the egress tunnel port. A tunnel can have as many tunnel ports as required to support the customer devices that need to communicate through the tunnel.
An egress tunnel port strips the 2-byte Ethertype field (0x8100) and the 2-byte length field and transmits the traffic with the 802.1Q tag still intact to an 802.1Q trunk port on a customer device. The 802.1Q trunk port on the customer device strips the 802.1Q tag and puts the traffic into the appropriate customer VLAN.
Note Tunnel traffic carries a second 802.1Q tag only when it is on a trunk link between service-provider network devices, with the outer tag containing the service-provider-assigned VLAN ID and the inner tag containing the customer-assigned VLAN IDs.
2.802.1Q Tunneling Configuration Guidelines and Restrictions
When configuring 802.1Q tunneling in your network, follow these guidelines and restrictions:
?Use asymmetrical links to put traffic into a tunnel or to remove traffic from a tunnel.
?Configure tunnel ports only to form an asymmetrical link.
?Dedicate one VLAN for each tunnel.
?Assign only tunnel ports to VLANs used for tunneling.
?Trunks require no special configuration to carry tunnel VLANs.
?Tunnel ports are not trunks. Any commands to configure trunking are inactive while the port is configured as a tunnel port.
?Tunnel ports learn customer MAC addresses.
?We recommend that you use ISL trunks to carry tunnel traffic between devices that do not have tunnel ports. Because of the 802.1Q native VLAN feature, using 802.1Q trunks requires that you be very careful when you configure tunneling: a mistake might direct tunnel traffic to a non-tunnel port.
?Ensure that the native VLAN of the 802.1Q trunk port in an asymmetrical link carries no traffic. Because traffic in the native VLAN is untagged, it cannot be tunneled correctly. Alternatively, you can enter the global vlan dot1q tag native command to tag native VLAN egress traffic and drop untagged native VLAN ingress traffic.
?Configure jumbo frame support on tunnel ports:
–See the "Configuring Jumbo Frame Support" section on page?9-10.
–Take note of the modules listed in the "Configuring Jumbo Frame Support" section that do not support jumbo frames.
?Jumbo frames can be tunneled as long as the jumbo frame length combined with the 802.1Q tag does not exceed the maximum frame size.
?Because tunnel traffic has the added ethertype and length field and retains the 802.1Q tag within the switch, the following restrictions exist:
–The Layer 3 packet within the Layer 2 frame cannot be identified in tunnel traffic.
–Layer 3 and higher parameters cannot be identified in tunnel traffic (for example, Layer 3 destination and source addresses).
–Because the Layer 3 addresses cannot be identified within the packet, tunnel traffic cannot be routed.
–The switch can provide only MAC-layer filtering for tunnel traffic (VLAN IDs and source and destination MAC addresses).
–The switch can provide only MAC-layer access control and QoS for tunnel traffic.
–QoS cannot detect the received CoS value in the 802.1Q 2-byte Tag Control Information field.
?On an asymmetrical link, the Cisco Discovery Protocol (CDP) reports a native VLAN mismatch if the VLAN of the tunnel port does not match the native VLAN of the 802.1Q trunk. The 802.1Q tunnel feature does not require that the VLANs match. Ignore the messages if your configuration requires nonmatching VLANs.
?Asymmetrical links do not support the Dynamic Trunking Protocol (DTP) because only one port on the link is a trunk. Configure the 802.1Q trunk port on an asymmetrical link to trunk unconditionally.
?The 802.1Q tunneling feature cannot be configured on ports configured to support private VLANs.
?The following Layer 2 protocols work between devices connected by an asymmetrical link:
–CDP
–UniDirectional Link Detection (UDLD)
–Port Aggregation Protocol (PAgP)
–Link Aggregation Control Protocol (LACP)
?PortFast BPDU filtering is enabled automatically on tunnel ports.
?CDP is automatically disabled on tunnel ports.
?VLAN Trunk Protocol (VTP) does not work between the following devices:
–Devices connected by an asymmetrical link
–Devices communicating through a tunnel
Note VTP works between tunneled devices if Layer 2 protocol tunneling is enabled. See Chapter?18, "Configuring Layer 2 Protocol Tunneling," for configuration details.
?To configure an EtherChannel as an asymmetrical link, all ports in the EtherChannel must have the same tunneling configuration. Because the Layer 3 packet within the Layer 2 frame cannot be identified, you must configure the EtherChannel to use MAC-address-based frame distribution.
The following configuration guidelines are required for your Layer 2 protocol tunneling configuration:
?On all the service provider edge switches, PortFast BPDU filtering must be enabled on the 802.1Q tunnel ports as follows:
Router(config-if)# spanning-tree bpdufilter enable
Router(config-if)# spanning-tree portfast
Note PortFast BPDU filtering is enabled automatically on tunnel ports.
?At least one VLAN must be available for Native VLAN tagging (vlan dot1q tag native option). If you use all the available VLANs and then try to enable the vlan dot1q tag native option, the option will not be enabled.
?On all the service provider core switches, tag native VLAN egress traffic and drop untagged native VLAN ingress traffic by entering the following command:
Router(config)# vlan dot1q tag native
?On all the customer switches, either enable or disable the global vlan dot1q tag native option.
Note If this option is enabled on one switch and disabled on another switch, all traffic is dropped; all customer switches must have this option configured the same on each switch.
The following configuration guidelines are optional for your Layer 2 protocol tunneling configuration:
?Because all the BPDUs are being dropped, spanning tree PortFast can be enabled on Layer 2 protocol tunnel ports as follows:
Router(config-if)# spanning-tree portfast trunk
?If the service provider does not want the customer to see its switches, CDP should be disabled on the 802.1Q tunnel port as follows:
Router(config-if)# no cdp enable
3.Configuring 802.1Q Tunneling
These sections describe 802.1Q tunneling configuration:
?Configuring 802.1Q Tunnel Ports
?Configuring the Switch to Tag Native VLAN Traffic
Caution Ensure that only the appropriate tunnel ports are in any VLAN used for tunneling and that one VLAN is used for each tunnel. Incorrect assignment of tunnel ports to VLANs can forward traffic inappropriately.
a)Configuring 802.1Q Tunnel Ports
To configure 802.1Q tunneling on a port, perform this task:
? Command Purpose
Step?1? Router(config)# interface type1 ?slot/port Selects the LAN port to configure.
Step?2? Router(config-if)# switchport Configures the LAN port for Layer 2 switching:
?You must enter the switchport command once without any keywords to configure the LAN port as a Layer?2 interface before you can enter additional switchport commands with keywords.
?Required only if you have not entered the switchport command already for the interface.
Step?3? Router(config-if)# switchport mode dot1q-tunnel Configures the Layer 2 port as a tunnel port.
Router(config-if)# no switchport mode dot1q-tunnel Clears the tunnel port configuration.
Step?4? Router(config-if)# end Exits configuration mode.
Step?5? Router# show dot1q-tunnel [interface type interface-number] Verifies the configuration.
1 type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet
This example shows how to configure tunneling on port 4/1 and verify the configuration:
Router# configure terminal
Router(config)# interface fastethernet 4/1
Router(config-if)# switchport mode dot1q-tunnel
Router(config-if)# end
Router# show dot1q-tunnel interface
b)Configuring the Switch to Tag Native VLAN Traffic
The vlan dot1q tag native command is a global command that configures the switch to tag native VLAN traffic, and admit only 802.1Q tagged frames on 802.1Q trunks, dropping any untagged traffic, including untagged traffic in the native VLAN.
To configure the switch to tag traffic in the native VLAN, perform this task:
? Command Purpose
Step?1? Router(config)# vlan dot1q tag native Configures the switch to tag native VLAN traffic.
Router(config)# no vlan dot1q tag native Clears the configuration.
Step?2? Router(config)# end Exits configuration mode.
Step?3? Router# show vlan dot1q tag native Verifies the configuration.
This example shows how to configure the switch to tag native VLAN traffic and verify the configuration:
Router# configure terminal
Router(config)# vlan dot1q tag native
Router(config)# end
Router# show vlan dot1q tag native
网络工程师成长日记354-某省邮政公司项目
网络工程师成长日记354-某省邮政公司项目这是我的第354篇原创文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人我就整点实在性的东西吧,也不废话了。下午五点多我在小寨等车回家,我想要老大的telephonenumber,于是... 查看详情
网络工程师成长日记358-北京安世亚太西安分公司网络改造项目
网络工程师成长日记358-北京安世亚太西安分公司网络改造项目这是网络工程师成长日记的第358篇连载文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人今天早上接到韩经理的电话说下午有个项目要和老大一块儿去,当... 查看详情
网络工程师成长日记327-房地产公司
网络工程师成长日记327-房地产公司这是我的第327篇原创文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人某房地产公司项目感想今天早上刚到公司就被老大训了,的确今天是来的有点迟了,没办法公交车难等啊!和他... 查看详情
网络工程师成长日记326-科拉斯项目回忆录
网络工程师成长日记326-科拉斯项目回忆录这是网络工程师成长日记的第326篇连载文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人今天公司接了一个西安的活,据说是给中企通信做的。顾客的地址是:华奥大厦科拉斯... 查看详情
网络工程师成长日记331-壳牌某分公司技术支持
网络工程师成长日记331-壳牌某分公司技术支持这是我的第331篇原创文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人延长壳牌石油有限公司某工程项目感想周四下午,前台说明天让我跟老大出去做个项目!!!心里就... 查看详情
网络工程师成长日记379-prada公司设备升级工程感想
网络工程师成长日记379-PRADA公司设备升级工程感想这是我的第379篇原创文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人11月21日下午接到老大的通知,下午有工程需要出去做。我有幸能跟着老大去做这个项目。我们的... 查看详情
网络工程师成长日记387-蒲城中铁20局项目回忆录
网络工程师成长日记387-蒲城中铁20局项目回忆录这是我的第387篇原创文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人5月4日早晨,接到公司通知,有三个项目是给火车站的设备安装,分别去往延安,榆林,蒲城。最... 查看详情
网络工程师成长日记369-中铁20局延安更换路由器项目
网络工程师成长日记369-中铁20局延安更换路由器项目这是我的第369篇原创文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人5月4号接到公司的电话,通知我第二天要去做个工程。带着激动就连忙答应了!想到第一次做... 查看详情
网络工程师成长日记357-某城市烟草局项目
网络工程师成长日记357-某城市烟草局项目这是我的第357篇原创文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人9月15号星期二下我与老大及合作网络公司李总、连总午坐车去往某城市,天气晴。此次前去某城市卷烟厂... 查看详情
网络工程师成长日记335-某市统计局
网络工程师成长日记335-某市统计局这是我的第335篇原创文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人老大急召回公司,没有办法,七点从西电回来还是和高工来到公司原来明天我们要去某市做项目了,这个让人很... 查看详情
网络工程师成长日记325-红牛西安工程回忆录
网络工程师成长日记325-红牛西安工程回忆录这是网络工程师成长日记的第325篇连载文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人红牛全国组网项目感想也许是幸运,也许是补偿吧!昨天在房地产公司的项目特让人... 查看详情
网络工程师成长日记325-红牛西安工程回忆录
网络工程师成长日记325-红牛西安工程回忆录这是网络工程师成长日记的第325篇连载文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人红牛全国组网项目感想也许是幸运,也许是补偿吧!昨天在房地产公司的项目特让人... 查看详情
网络工程师成长日记321-阿克苏诺贝尔工程感想
网络工程师成长日记321-阿克苏诺贝尔工程感想这是网络工程师成长日记的第321篇连载文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人西安市高新区创业广场阿克苏诺贝尔International油漆公司”10点多,老大找人去做项... 查看详情
网络工程师成长日记322-阿克苏诺贝尔油漆苏州公司西安分公司工程回忆录
网络工程师成长日记322-阿克苏诺贝尔油漆苏州公司西安分公司工程回忆录这是网络工程师成长日记的第322篇连载文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人今天和老大去阿克苏诺贝尔油漆苏州公司西安分公司做... 查看详情
网络工程师成长日记333-某城市政府项目
网络工程师成长日记333-某城市政府项目这是我的第333篇原创文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人直接上干货,拓扑图:工程目的:排除故障配置如下:LinWei#showrunning-configBuildingconfiguration...Currentconfiguration... 查看详情
网络工程师成长日记390-某地防火墙项目
网络工程师成长日记390-某地防火墙项目这是网络工程师成长日记的第390篇连载文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人接到了一个急促的电话,我们很快到了汽车站,坐上了去往商南的汽车沿路风景是如此的... 查看详情
网络工程师成长日记339-联合利华项目
网络工程师成长日记339-联合利华项目这是我的第339篇原创文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人西安联合利华网络改造我是个大菜鸟,还没有入行,头一天接到老大的电话,说十九号去联合利华,有个项目要... 查看详情
网络工程师成长日记402-乌审旗某采气厂项目
网络工程师成长日记402-乌审旗某采气厂项目这是网络工程师成长日记的第402篇连载文章,记录网络工程师行业的点点滴滴,结交IT行业有缘之人7日晚,接上级通知,要去榆林参加一次项目。由我带领郑工,当然其他的几位工程... 查看详情